-
-
Notifications
You must be signed in to change notification settings - Fork 693
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Canned query permissions mechanism #800
Comments
|
Maybe #801 (configuring permissions with a SQL query) is enough here - might not need this mechanism at all, since that mechanism covers it. |
|
It's a bit obscure though. I'll try building both and see how they feel in practice. |
|
I like this mechanism better than the SQL query one. Constructing SQL queries that return true if a particular string is embedded inside a JSON list in a larger object is decidedly non-trivial. |
|
I'm going to implement this documentation-first. |
|
I should add the '*' bit to the docs. |
|
Next step: a utility function and tests for matching actors to allow blocks. |
|
Documentation for |
|
Now the actual permission checks. I need these in two places: the code that generates the list of available queries on https://latest.datasette.io/fixtures#queries and the query page itself at https://latest.datasette.io/fixtures/pragma_cache_size |
|
In the code that's: datasette/datasette/views/database.py Lines 56 to 64 in 9c563d6
And: datasette/datasette/views/database.py Lines 98 to 112 in 9c563d6
|
|
This is implemented and documented: https://datasette.readthedocs.io/en/latest/authentication.html |
|
I didn't build this quite right: it should be using the permissions plugin hook. |
|
See #810 for work to finish this. |
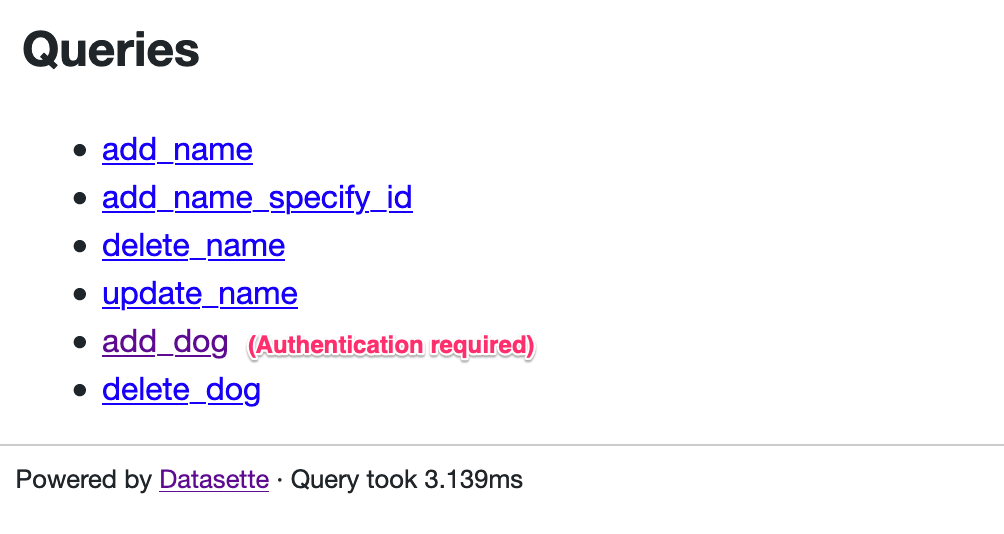
Originally posted by @simonw in #698 (comment)
The text was updated successfully, but these errors were encountered: