-
-
Notifications
You must be signed in to change notification settings - Fork 2.7k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
"Certificate not standards compliant" on macOS Catalina, iOS 13 #174
Comments
|
Looks like it's a new limit on maximum lifespan. See https://support.apple.com/en-us/HT210176.
It's surprising they would enforce it on private roots, honestly. I am mildly tempted to fake the notBefore, but one way or another I need to fix it soon, or a bunch of certificates will be generated that will stop working after updating to Catalina. BTW, if you try Chrome Canary it should give you a better error message. |
|
I opted to backdate the notBefore until the ACME server is implemented. Once ACME is an option, automation should reduce the need for long lifespans. @selfagency Please test the latest master ( |
|
I've recently had this issue as well. Tried the |
|
I'm having a same issue with Chrome on MacOS Catalina public beta 2! Interestingly certificate works on Firefox developer edition 🤷♂️ Tried running ➜ brew install mkcert --HEAD --debug
/usr/local/Homebrew/Library/Homebrew/brew.rb (Formulary::FormulaLoader): loading /usr/local/Homebrew/Library/Taps/homebrew/homebrew-core/Formula/mkcert.rb
Error: can't modify frozen String
/usr/local/Homebrew/Library/Homebrew/exceptions.rb:475:in `initialize'
/usr/local/Homebrew/Library/Homebrew/formula_installer.rb:86:in `new'
/usr/local/Homebrew/Library/Homebrew/formula_installer.rb:86:in `prevent_build_flags'
/usr/local/Homebrew/Library/Homebrew/cmd/install.rb:134:in `install'
/usr/local/Homebrew/Library/Homebrew/brew.rb:102:in `<main>'➜ brew --version
Homebrew 2.1.7
Homebrew/homebrew-core (git revision 276f; last commit 2019-07-10)Why Apple is limiting certs validity to 825(Magic number?) days though? 🤔 |
|
Same deal, unfortunately, with the |
|
825 comes from the CAB forum bylaws for certificates. All of the major products and CA's follow them. |
Manually compiling from current master using go on MacOS Catalina public beta 2 works on chrome 🎉 brew install go
go get -u github.com/FiloSottile/mkcert
$(go env GOPATH)/bin/mkcert -install
$(go env GOPATH)/bin/mkcert localhost |
That works for me on macOS Catalina too. |
|
Feeling anxious to get this into a release. I'll think about how I can test, maybe Parallels macOS upgraded to Catalina. |
|
If you use APFS, you can install it into its own container. https://www.macworld.com/article/3405588/how-to-install-the-macos-catalina-beta-in-its-own-apfs-container.html
…On Jul 31, 2019, 3:27 PM -0400, Randy Fay ***@***.***>, wrote:
Feeling anxious to get this into a release. I'll think about how I can test, maybe Parallels macOS upgraded to Catalina.
—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHub, or mute the thread.
|
|
Sadly, I'm unable to verify that latest works on Catalina. I've tried a number of things and have failed at every step. I built mkcert with
No matter what I do I end up with a cert that has a 2029 expiration date and is thus "revoked". I assume there's some cleanup step I've missed. I certainly see the important commit df15e0c there. Suggestions on what I could do differently to verify this? |
|
I confirm this situation with a better test.
I will try to do some debugging to see why the code that looks so good is not getting us to a shorter expiration. |
|
The code wasn't trying to make a shorter expiration, but to backdate the Not Before so the certificate would be exempt. I finally have time and space to install Catalina and will get to testing today or tomorrow. |
|
And... I spent a lot more time with it tonight, and tried the shorter expiration because of the conversation here. But I discovered I had a lot more complex environment than I was remembering. (A linux mkcert in a container was using the root CA created on macOS, which the macOS browser had to trust... but I was still using the old linux mkcert) Now I can confirm that the code in 2d05f3b does work. I didn't understand at all given the conversation here how we could still be making 10 years work. I'd rather do the more obvious code in https://github.com/rfay/mkcert/blob/7642e8ce4edbd274ee79b788423c05e3765a4cc8/cert.go#L67-L75, as it directly addresses the issue here. I'll make a PR of that if you like it. But I think my earlier testing was flawed due to the complexity of my own environment and the disconcerting fact we are still using a 10 year expiration, which I thought was the issue. |
|
I went ahead and made the PR. We'll see if it's useful. I think it's a more direct approach to this problem. #187 Thanks for all your work on this! It means so much to so many of us. |
|
Had to kick macOS to get it to download Catalina, but I managed to test this. The fix works correctly. Here's a before and after. I'll make a release tomorrow. (What didn't work is |
|
Fixed in v1.4.0. https://github.com/FiloSottile/mkcert/releases/tag/v1.4.0 |
|
How can I install v1.4.0 before it comes through Brew? Is there some magic command or do I need to take the |
|
You can get binaries from the release page. https://github.com/FiloSottile/mkcert/releases/tag/v1.4.0 |
|
Homebrew has 1.4.0 now. |
Thx Filo. After spending hours to figure out why my self signed cert is not acceptable only on chrome I read your post. Get a new cert with only 2 years and everything works. Edit: Before my Cert was valid for 3 years and Chrome always showed "NET::ERR_CERT_REVOKED" |
|
I'm still having issues with this. :-( If I regenerate certs from scratch, both the root and the leaf have a notBefore of today, and I'm getting This is with: |
Reinstalling a few times using Homebrew didn't work. I ended up compiling from scratch. Is it possible the binary 1.4.0 Homebrew distribution has the old version of the code? |
|
AFAIK the Homebrew distribution is the right version. Maybe you had an old version built from source higher in your $PATH? If you can reproduce this from scratch please open a new issue so we don't lose track of it. |
|
@arimolzer I believe the screenshot here is of the Root Certificate Authority, and not the end-entity/leaf certificates, where this issue becomes an issue. I.e. if you run: You should see that this end-entity/leaf certificate, which you would use in your application, are properly back dated. So far I haven't seen an issue with having Root Certificate Authorities create certificates with start dates before its own creation date; however, I'm sure it's only a matter of time before Apple's security theater becomes more problematic. |
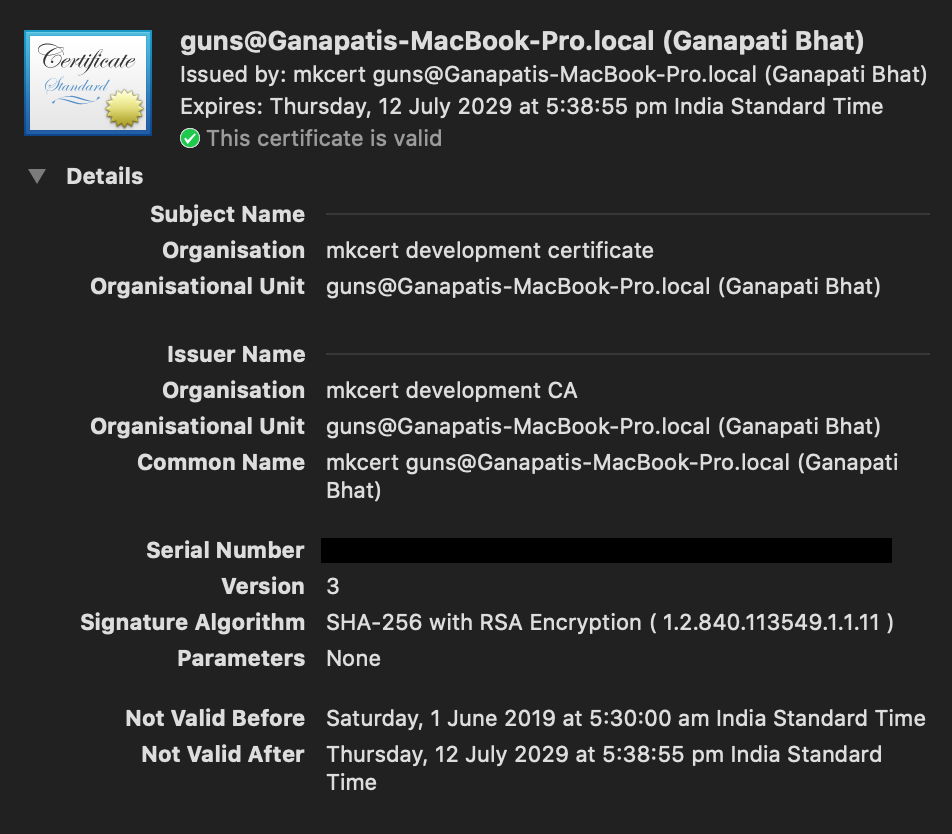

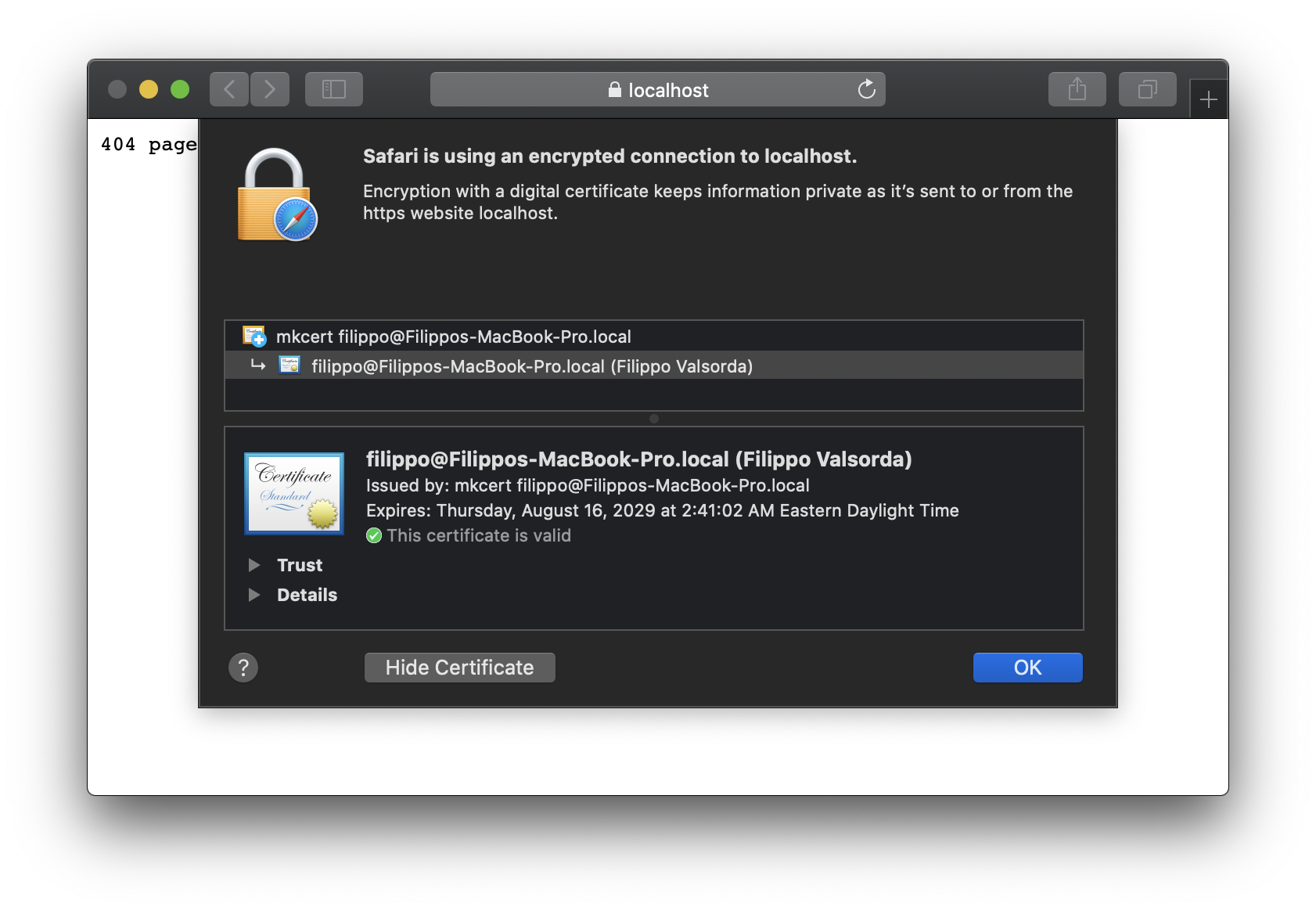


Certificates generated after July 1st, 2019 by versions of mkcert prior to v1.4.0 will not work on macOS 10.15 Catalina and iOS 13. Please update mkcert and regenerate the affected certificates.
The root CA is unaffected and there is no need to rerun
mkcert -install.— @FiloSottile
Under MacOS Catalina Public Beta 2, after installing mkcert via Homebrew and running the root certificate installer, my mkcert generated certificates are rejected in Safari with the message 'Certificate is not standards compliant' and in Chrome with 'ERR_CERT_REVOKED'.
The text was updated successfully, but these errors were encountered: