PSWinReporting is a little PowerShell module that solves the problem of monitoring and reading Windows Events. It allows you to set up monitoring of Domain Controllers (and from 2.X any other servers) for events that happen on them. By default, it comes with built-in Active Directory events supports, but since 2.0 you can configure it to monitor anything. You can set up reporting on any types of events and have emails delivered with a summary of hourly, daily, weekly, monthly, or quarterly changes. It also supports sending notifications to Microsoft Teams, Slack, and Discord. Make sure to go thru related articles as they have all the KNOW HOW which is quite useful if you want to get everything from this module.
The full project description is available on my website - Full project description.
Currently, there are 2 branches of PSWinReporting.
- Legacy branch - available in PS Gallery as PSWinReporting -
Install-Module -Name 'PSWinReporting' -Force - Master branch - available in PS Gallery as PSWinReportingV2 -
Install-Module -Name 'PSWinReportingV2' -Force
I've decided that both PowerShell modules can coexist together, especially for scenarios for people who want to switch, but don't want to do it right away. This way, you can keep using old version as is, and slowly fix your other stuff, or use new Find-Events command. I've slightly renamed the commands for V2 release.
Master edition is a complete rewrite and a new beginning. It provides the same functionality as Legacy 1.X version and then some more.
- Ability to translate report and have it suite your needs
- Ability to completely modify events monitoring
- Ability to monitor any servers, for any events using simple to use schema
- Ability to target multiple servers, computers or files at the same time
-
2.0.20 - 30.01.2020
- Fix for executing Discord/Slack or Teams if it's not in use during Trigger
-
2.0.19 - 28.01.2020
- Fix for DatesRanges using cached values
- Fix for Ldap* reports always running even when not requested
-
2.0.18 - 20.01.2020
- Fix for detecting forest/domains
-
2.0.17 - 19.01.2020
- Added LdapBindingsDetails
- Added LdapBindingsSummary
-
2.0.16 - 12.01.2020
- Fix for typos
-
2.0.15 - 11.01.2020
- Simplified, enhanced
New-WinSubscriptionTemplates(see examples) - Some engine fixes
- Simplified, enhanced
-
2.0.14 - 11.09.2019
- Fixed New-WinSubscriptionTemplates
-
2.0.13 - 30.08.2019
- Find-Events
- Fix for Target not having anything to run
- Fix for Files being passed even thou - not existing
- Fix for Reports variable not being available during non-standard runs
- Removed definitions
- ADEventsReboots
- Added definitions
- OSStartupShutdownCrash
- OSCrash
- NetworkAccessAuthenticationPolicy
- Changed .psd1 required modules to have specific required version. Less likely things will be broken during update of other modules.
- Fixes for Reporting based on ForwardedEvents
- Find-Events
-
2.0.12 - 09.07.2019
- Small fixes
-
2.0.11 - 15.06..2019
- Find-Events
- Fix for Group Policy Events
- Fix for Subevents within Events overwriting values
- Fix for output when using Definitions/Times/Servers (1 definition returns an Array, 2 or more returns hashtable of Arrays)
- Find-Events
-
2.0.10 - 06.05.2019
- Fixes for reporting
- Adding subscriptions
At this moment there is no documentation for PSWinReportingV2 except for those articles below. Feel free to explore Examples if you're eager to try the new version — otherwise fallback to PSWinReporting Legacy Edition.
PSWinReporting comes with predefined, built-in reports. Those are for Find-Events. Those also come defined in example configuration script which you can use straight away after verifying everything is as per your requirement.
- ADComputerChangesDetailed
- ADComputerCreatedChanged
- ADComputerDeleted
- ADGroupChanges
- ADGroupChangesDetailed
- ADGroupCreateDelete
- ADGroupEnumeration
- ADGroupMembershipChanges
- ADGroupPolicyChanges
- ADLogsClearedOther
- ADLogsClearedSecurity
- ADUserChanges
- ADUserChangesDetailed
- ADUserLockouts
- ADUserLogon
- ADUserLogonKerberos
- ADUserStatus
- ADUserUnlocked
- ADOrganizationalUnitChangesDetailed (added in 2.0.10)
- OSStartupShutdownCrash (added in 2.0.12) - covers startup, shutdown and crashes - probably needs some work on the engine later on to allow field merging
- OSCrash (added in 2.0.12) - covers system crashes
- NetworkAccessAuthenticationPolicy (added in 2.0.12) - covers authorizations approved/denied for WIFI and ETHERNET
PSWinReporting comes with predefined report times. This means you can use True/False to enable/disable period. In case of Find-Events, you can use defined times (checked only) from DatesRange parameter.
- CurrentDay
- CurrentDayMinusDayX
- CurrentDayMinuxDaysX
- CurrentHour
- CurrentMonth
- CurrentQuarter
- CustomDate
- Everything
- Last14days
- Last3days
- Last7days
- OnDay
- PastDay
- PastHour
- PastMonth
- PastQuarter
Of course, you can also define DateFrom, DateTo parameters for custom use when using Find-Events command.
Legacy edition will continue it's life as 1.X.X. If you want to keep on using it, feel free, but it's highly encouraged to use 2.x.x when it's fully functional with all features. Code is available as Legacy Branch. Following links can help in understanding how it works and how to set it up:
- Review of features coming in 2.0 along with some features description for the current version - Overview of configuration and features.
- Review of new features in PSWinReporting 1.7 - Lots of changes, review required. Microsoft Teams, Slack, SQL and forwarders support
- Review of new features in PSWinReporting 1.0 - Lots of changes, review required.
- Last version of Get-EventsLibrary.ps1 - This is the actual code base for the old version. Just in case…
- Blog post about version 0.8 - Updates from feedback. Last version before the name change.
- Blog post about version 0.7 - Updates from feedback.
- Blog post about version 0.6 - Updates from feedback.
- Blog post about initial version and the differences in monitoring approach
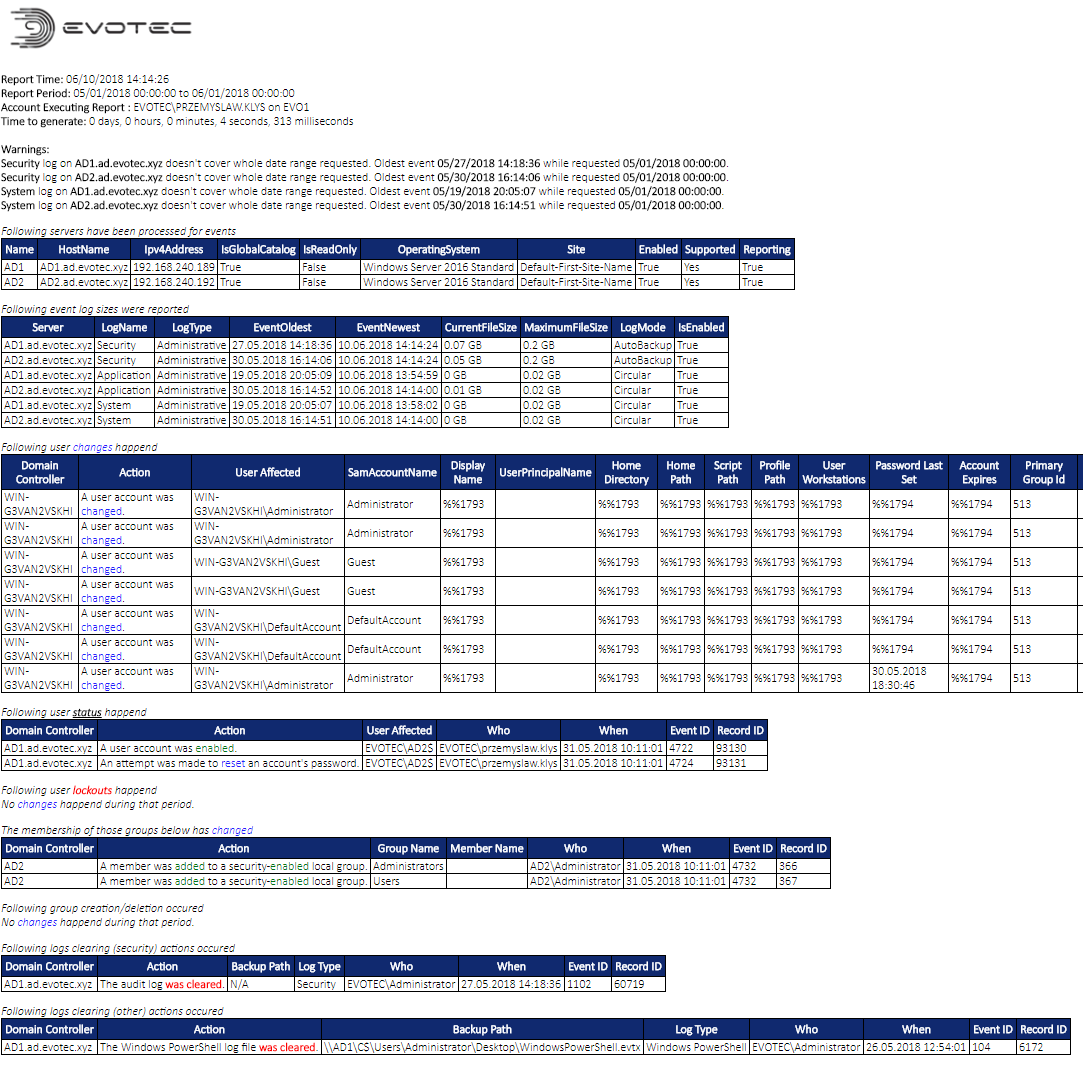
Following AD Events are supported:
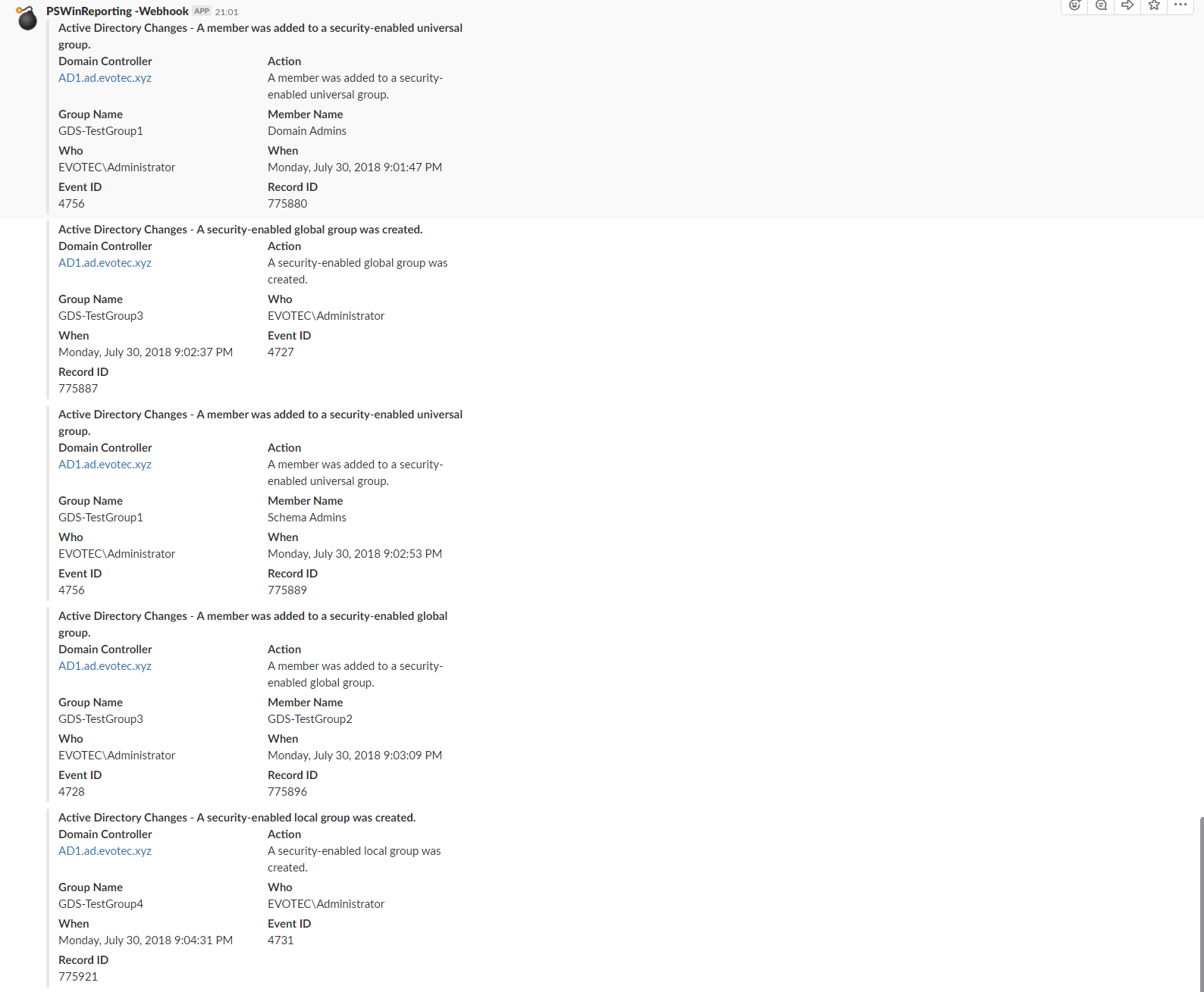
- Group create, delete, modify (Who / When / What)
- Group membership changes (Who / When / What)
- User changes (Who / When / What)
- User created / deleted (Who / When)
- User password changes (Who / When)
- User lockouts (Who / When / Where)
- Computer Created / Modified (Who / When / Where)
- Computer Deleted (Who / When / Where)
- Event Log Backup (Who / When)
- Event Log Clear (Who / When)
Features:
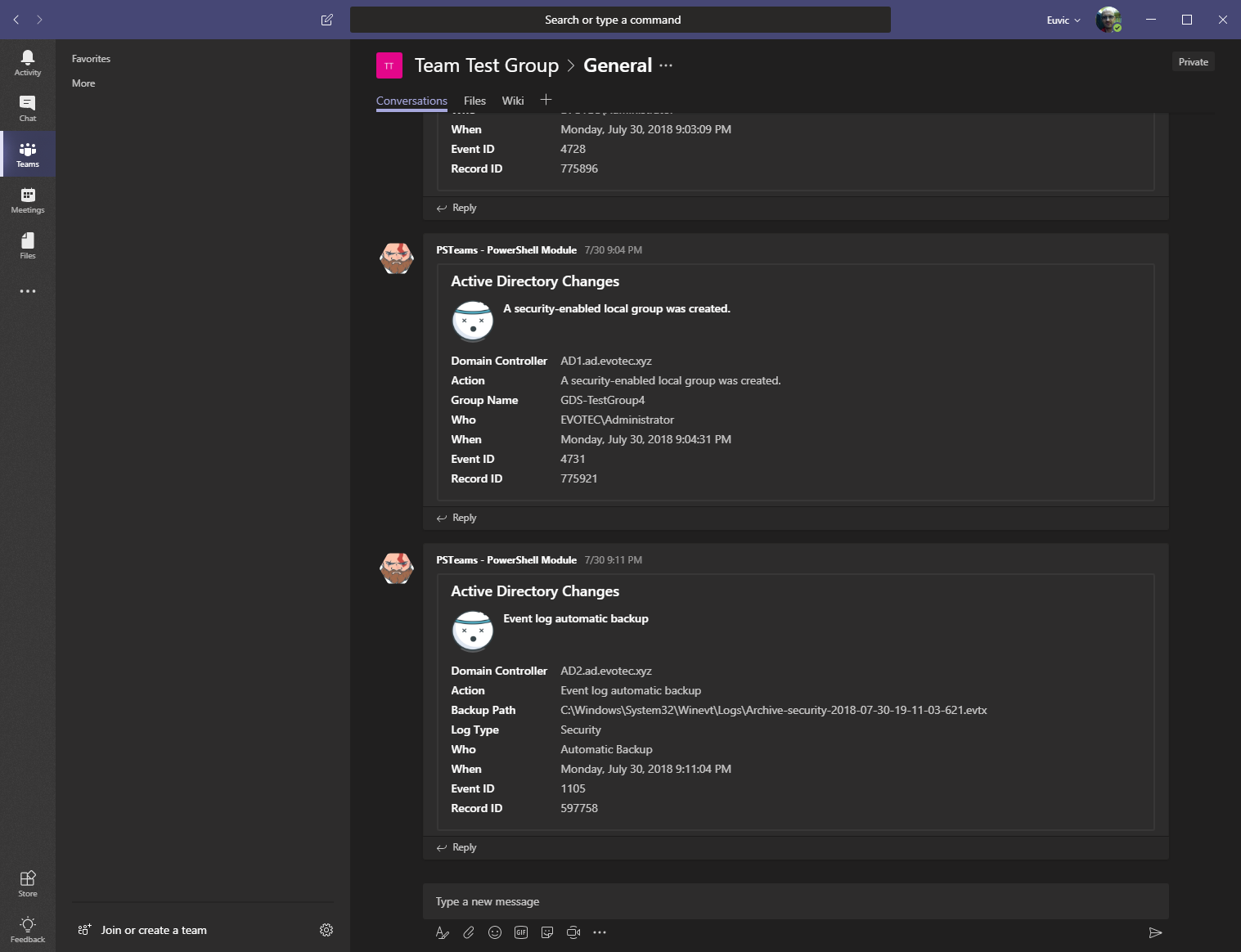
- Support for Event Forwarding - monitoring one event log instead of scanning all domain controllers
- Support for Microsoft Teams - Sending events as they happen to Microsoft Teams (only supported when forwarders are in use)
- Support for Slack - Sending events as they happen to Slack (only supported when forwarders are in use)
- Support for Microsoft SQL - Sending events directly to SQL (some people prefer it that way)
- Support for backing up old archived logs (moves logs from Domain Controllers into chosen place)
- Support for re-scanning logs from files - a way to recheck your logs for missing information