-
-
Notifications
You must be signed in to change notification settings - Fork 243
Getting Started
| Azure (Public) | Azure China | Azure Government |
|---|---|---|
Learn more at https://registry.terraform.io/modules/shibayan/keyvault-acmebot/azurerm/latest
Learn more at https://github.com/shibayan/keyvault-acmebot/issues/427
Acmebot allows you to select the ACME CA that will issue the certificate in the configuration. Currently, the following CAs have been verified to work.
-
Let's Encrypt
https://acme-v02.api.letsencrypt.org/directory
-
Buypass Go SSL
https://api.buypass.com/acme/directory
-
ZeroSSL (Requires EAB Credentials)
https://acme.zerossl.com/v2/DV90/
-
Google Trust Services (Requires EAB Credentials)
https://dv.acme-v02.api.pki.goog/directory
-
SSL.com (Requires EAB Credentials)
- For RSA:
https://acme.ssl.com/sslcom-dv-rsa - For ECDSA:
https://acme.ssl.com/sslcom-dv-ecc
- For RSA:
- Entrust (Requires EAB Credentials)
Note
Additional configuration is required when using ACME CA where EAB is required. Please refer to the following document for details.
Update the following configuration settings of the Function App:
-
Acmebot:VaultBaseUrl- DNS name of the Azure Key Vault (if you are using an existing Key Vault)
-
Acmebot:Webhook- Webhook destination URL (optional, Slack and Microsoft Teams are recommended)
- Message will be sent when the process succeeds or fails
-
Acmebot:PreferredChain- Set the CA name of the certificate chain you wish to use (optional)
-
Acmebot:MitigateChainOrder- Set to true, you can avoid incorrect order in the Application Gateway (default:
false)
- Set to true, you can avoid incorrect order in the Application Gateway (default:
-
Acmebot:RenewBeforeExpiry- Set the number of days to renew a certificate before it expires (default: 30)
-
Acmebot:UseSystemNameServer- Set to true, Use App Service default DNS for domain validation instead of external DNS (default:
false)
- Set to true, Use App Service default DNS for domain validation instead of external DNS (default:
-
Acmebot:DefaultSigner- Specifies the default algorithm to be used in ACME requests. This option is effectively for Entrust (optional)
There are also additional settings that will be automatically created by Key Vault Acmebot:
-
Acmebot:Endpoint- The ACME endpoint used to issue certificates
-
Acmebot:Contacts- The email address (required) used in ACME account registration
For instructions on how to configure each DNS provider, please refer to the following page.
https://github.com/shibayan/keyvault-acmebot/wiki/DNS-Provider-Configuration
- Amazon Route 53
- Azure DNS
- Cloudflare
- DNS Made Easy
- Gandi LiveDNS
- GoDaddy
- Google Cloud DNS
- TransIP DNS
- Custom DNS Provider
You must enable Authentication on the Function App that is deployed as part of this application.
In the Azure Portal, open the Function blade then select the Authentication menu and enable App Service authentication. Click on the Add identity provider button to display the screen for adding a new identity provider. If you select Microsoft as your Identity provider, the required settings will be automatically filled in for you. The default settings are fine.

Make sure that the App Service Authentication setting is set to Require authentication. The permissions can basically be left at the default settings.

Note
If you are using Sovereign Cloud, you may not be able to select Express. Enable authentication from the advanced settings with reference to the following document.
Finally, you can save your previous settings to enable App Service authentication.
Open the access policy of the Key Vault and add the Certificate management access policy for the deployed application.
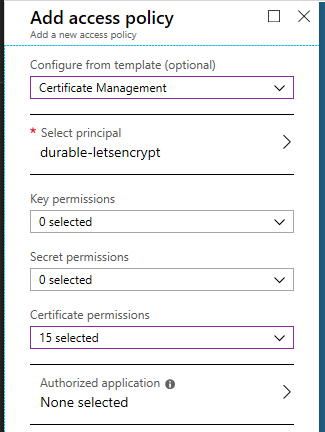
Access https://YOUR-FUNCTIONS.azurewebsites.net/dashboard with a browser, you will see a list of certificates managed by Acmebot. From this dashboard, you can easily issue new certificates and renew and revoke existing ones.

The dashboard feature is currently in preview. If you have any bugs or feature suggestions, please let us know in issue #341.